Threat Modeling healthcare delivery software and application: An
introduction
The
goal of any threat model process is to be able to determine as many threats
that could exploit identified vulnerabilities of the organization’s information
system. A software-focused threat model process seeks to identify and address
the threats that would attack the company’s information system by exploiting
the weaknesses or “vulnerabilities in the software components that are used by
the application, the operative systems software that the application uses and
the vulnerabilities of the underlying network and data infrastructure in which
these applications operate” (Morana, M., M. & Ucedavelez, p.6, 2015).
Threat modeling is a structured systematic approach that is either
software-focused, attacker-focused, or asset-focused to understand how
different threats could be realized by threat agents It
simulates how a successful compromise could take place. A threat agent is “an
intruder accessing the network via port on the firewall, a process assessing
data in a way that violates the security policy, a tornado wiping out a
facility, or an employee making an unintentional mistake that could expose
confidential information” (Harris, S., pp.1108, 26, 2013).
In the
healthcare delivery sector, as a result of the criticality of e-PHI
(electronic-protected patient health information) software vulnerabilities provide
exploitable weaknesses (attack surface) for threat agents to launch attack to
achieve specific goals, like stealing important personal or confidential
patient information. This can be achieved by the attacker injecting malicious SQL
codes in the healthcare delivery system application web pages after doing a
vulnerability scan. The goal is to gain unauthorized access into the database
storing e-PHI. It is, therefore, imperative to begin to address security risk
issues during the SDLC of the software or application design and production. A
good way of handling this is a structured, software-focused threat modeling
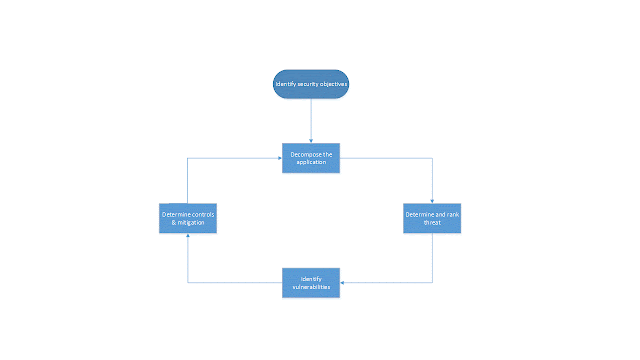
approach. Fig. 1.1 is the DFD (Data Flow Diagram) that decomposes the threat
modeling process steps involved in security design in the software development
life cycle.
Step 1
– Decompose the application
Step 2
- Determine and rank threats
Step 3
– Identify vulnerabilities
Step 4
– Determine controls or countermeasures and mitigation,
Software-focused
threat model process that uses trust boundaries (“any place where various
principals come together or where entities with different privileges interact”
– Shostack, A, p.50, 2014) identifies appropriate, effective and timely
countermeasures to deploy to mitigate attack on the healthcare delivery
information system. Why software-centric
modeling approach? This provides a better security on assets, and strong
defense against the attacker as security considerations are appropriately
included in the software design or system being built. A good explicit threat
model would document models of UML diagrams, APIs, and architecture.
References
Morana, M., M. &
Ucedavelez, T. Application Threat Modeling: Process for Attack
Simulation
and Threat Analysis. Wiley-Blackwell. (2015-28-5).
Harris, S. CISSP All-in-one
Exam Guide. 6th ed. McGraw Hill Education. (2013).
New
York.
Shostack, A. Threat Modeling:
Designing for Security. John Wiley & Sons, Inc. (2014).
Indianapolis.
No comments:
Post a Comment